Microsoft Entra IDs
Identity and Access Management
for a Zero Trust World
Secure every identity and access point across hybrid and multi-cloud environments. From adaptive authentication to least-privilege access, we implement IAM strategies that align with Zero Trust principles, so your business stays agile and protected.
48%
Improvement in access governance
40%
Reduction in lateral movement risks
- Home
- »
- Main Services
- »
- Identity and Access Management
Problem Use Case
Control Who Accesses What, When, and How?
Protect sensitive systems while enabling seamless, secure user access
- Access Control
- Seamless Authentication
-
Unauthorized Access Prevention Control and verify user identities. Block malicious or accidental access to sensitive systems.
-
Centralized Identity Governance Streamline identity lifecycle management across cloud and on-prem. Ensure consistent access policies.
-
Frictionless User Experience Enable secure, single sign-on and adaptive authentication. Balance protection with seamless access.
Services
Strengthen Your Security Posture
Across Cloud, Code & Compliance
Comprehensive solutions designed to secure every layer of your digital environment
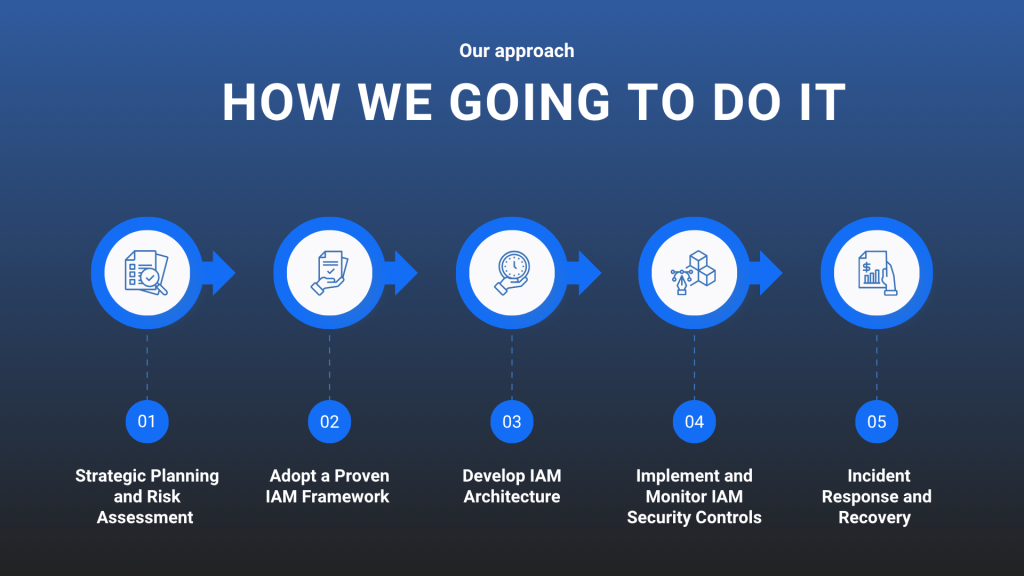
Why business need it
Why Businesses Need Modern IAM Solutions
Identity is the new security perimeter. IAM enables secure access across users, apps, and data, powering productivity while minimizing risk.
Lead Securely in the Cloud
Workshops
Our focused workshop helps define your identity management strategy, strengthen authentication, and align IAM practices with Zero Trust principles.
- MFA, SSO & Conditional Access (2 Weeks)
- Identity Governance & Lifecycle Management (2 Weeks)
- Zero Trust Readiness & Policy Design (2 Weeks)
Assessment
Evaluate your current IAM environment. Identify gaps in identity protection, user access controls, and Zero Trust alignment.
Accelerators
Kickstart your IAM journey with pre-built policy packs, governance templates, and conditional access frameworks tailored to your business needs.
Contact Us
Secure Access Starts with Identity
Connect with our IAM experts to design, deploy, and manage a Zero Trust-ready identity and access framework tailored to your business.
